Find The Easy Pass is one of the Hack The Box Reversing challenge,
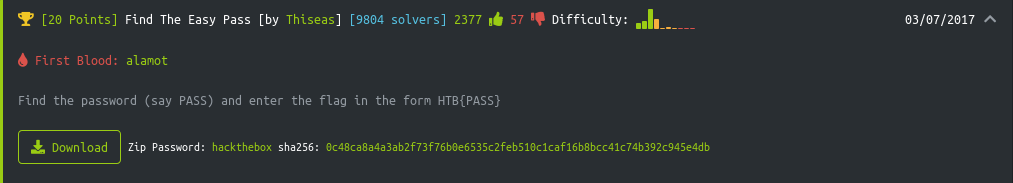
Tools used:
- Wine
- OLLYDBG
So let's start this by Downloading the file,
Unzip the file, you can see
Now lets unzip the file so we can see whats in it using OLLYDGB. It prompts for password,
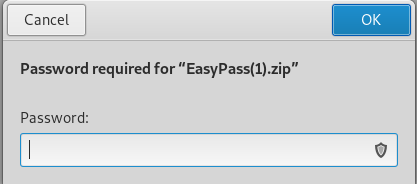
if you were wondering for the password here you can see that in the main site it had all the information!!
So, Since we required wine to use OLLYDGB, lets copy the extracted file to the like folder like shown in the figure
Done copying so lets open the file in OLLYDGB
now we got this lets search for some texts
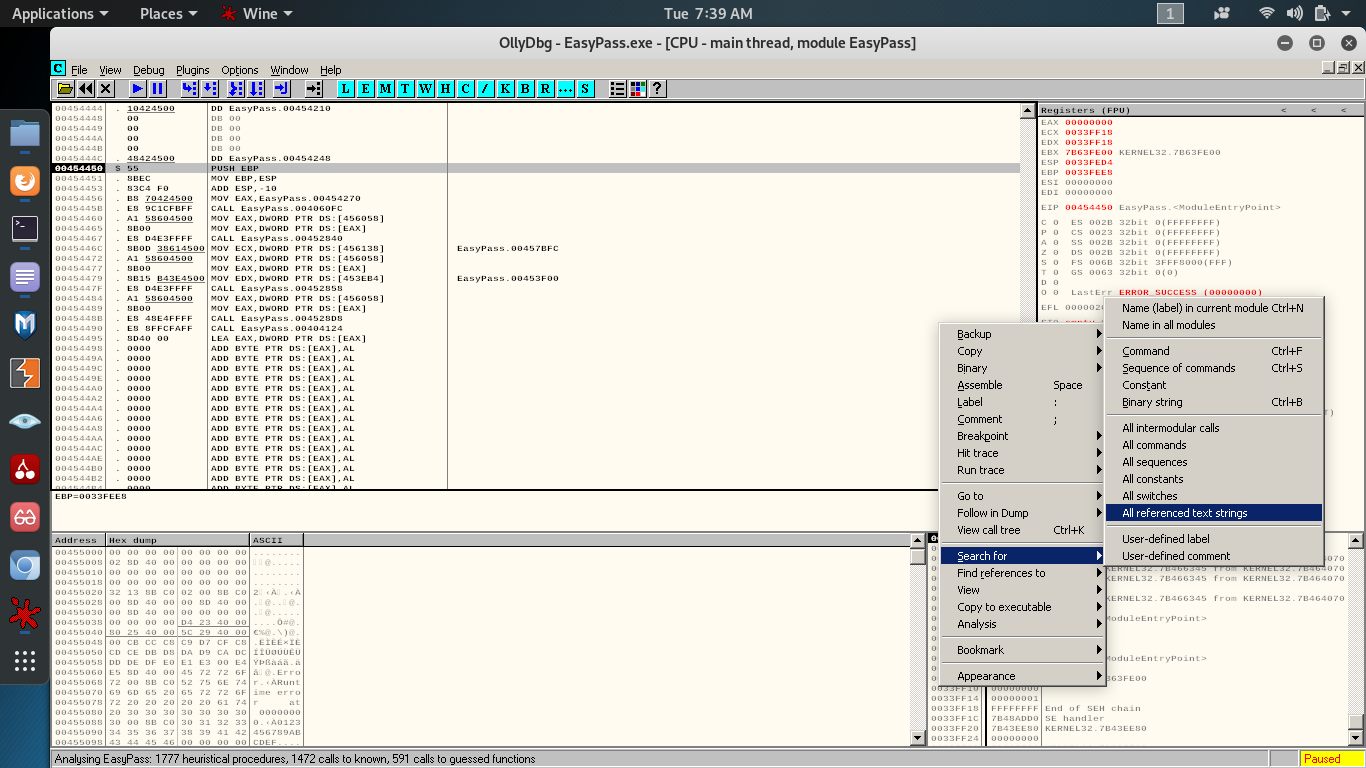
steps to get All referenced text strings:
- right click
- go to search for
- click on All referenced text strings
now,
looking at the strings, i found two great strings
Good job, Congratulations
Wrong Password
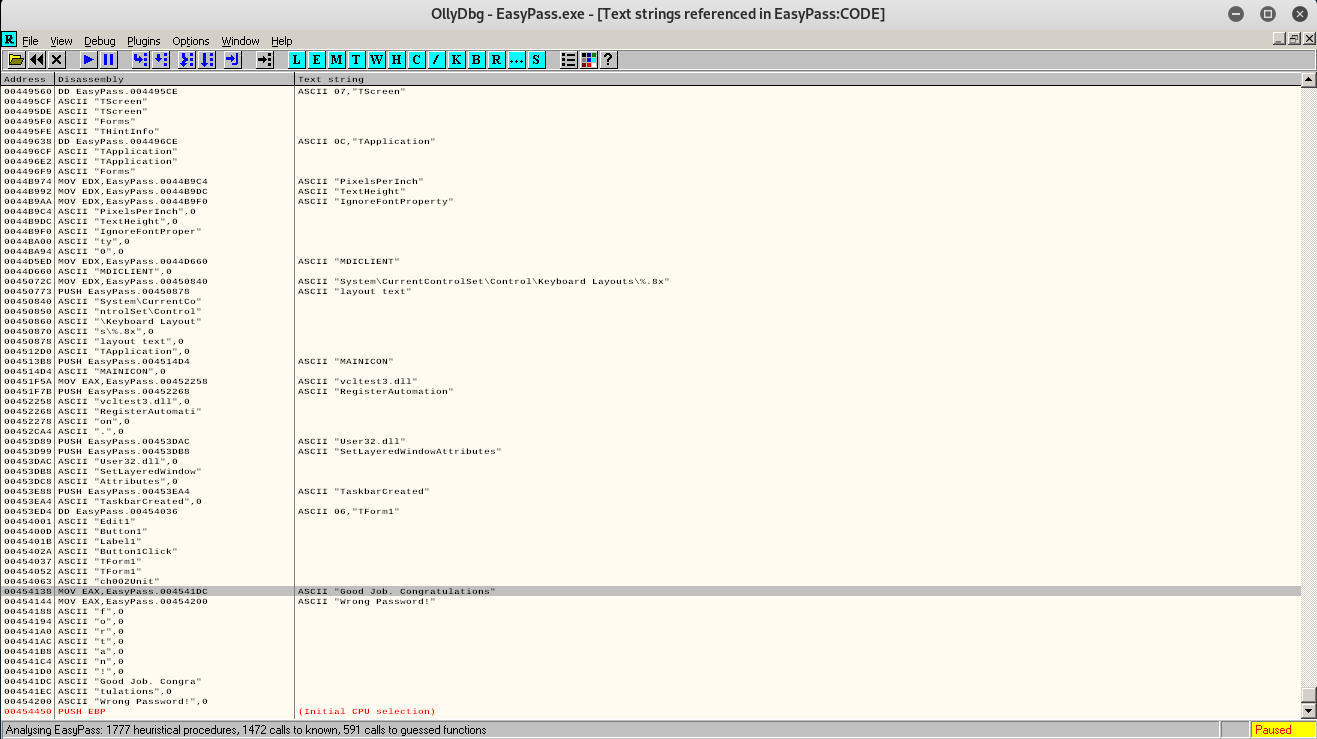
lets double click on wrong password to see whats going on there
if you may be wondering how the text font changed then,
1)Right click on the blank space
2)Click on Appearance ( the last option )
3)then goto Font and choose the font you like
now in the image above, we can see stuffs going on
you can see a JNZ assembly above the ASCII "Good Job. Congratulations"
As you know JNZ is a conditional jump, lets single left click on the JNZ and press enter,
It goes to 00454144

Now, we see that the condition is that if the password is wrong then its gonna jump to the Wrong password stuff.
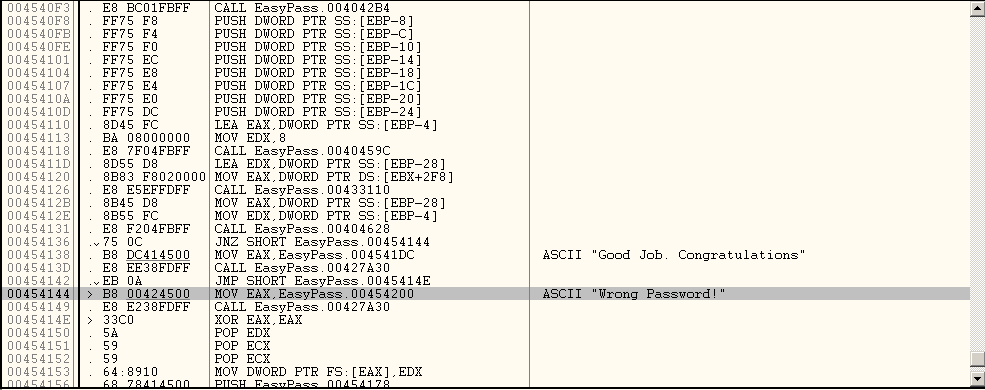
Lets set a Breakpoint at the CALL part.
so to set a Breakpoint you need to
double left click in the 2nd is and you will get the binary highlighted as in the image
now lets run the exe
It prompts for the password,
type anything you want
now click check password
looks like something poped up in the Registers
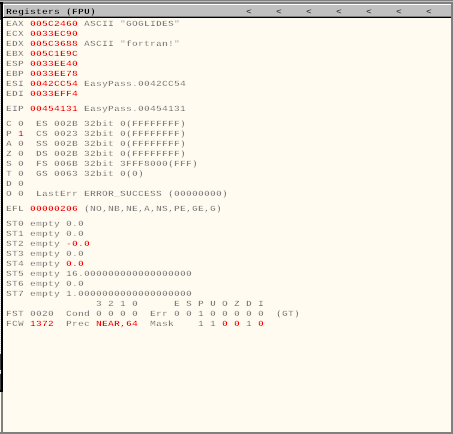
so what happened here is
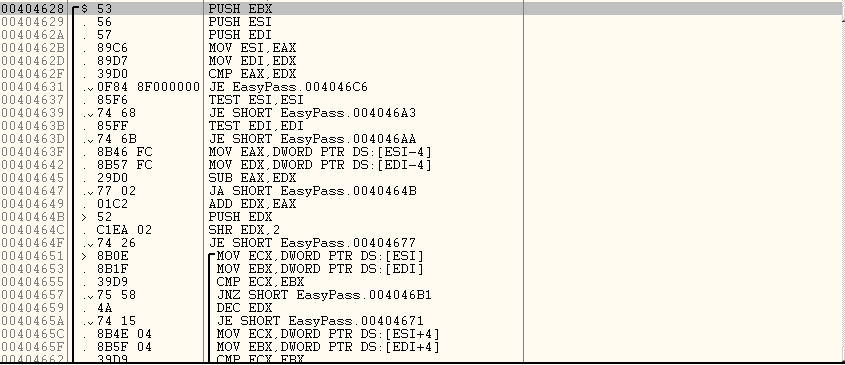
you can see the line
CMP EAX,EDX
It compares the EAX which was GOGLIDES in this case and EDX had fortran! which is the password for the EasyPass.exe
What actually happened there?
You can see that the EAX has been moved to ESI and followed by EDX moving to EDI.
then there is a comparison between EAX and EDX
If the comparison is successful or you have entered the right password in this context which is supposed to be fortran!, it jumps to 004046C6
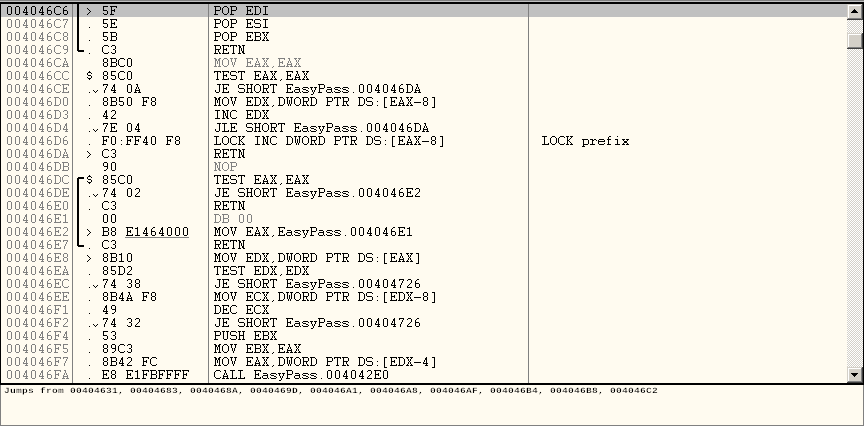
Here the values are POPed which means that the value are restored and following the functions, the function RETN or returns.
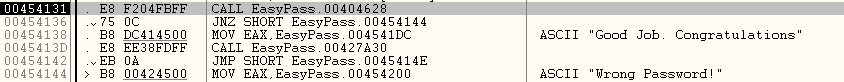
then as we have already talked before, with the correct password, the JNZ or the conditional jump is skipped and you get the message
"Good Job. Congratulations"

